Hi Kevin,
I appreciate your help and interest in my problem. I agree the mDNS RFC and its implementation are complex and I am not confident in making changes to mDNSResponder. I have some images (before and after the proposed 'fix') of the mDNS subsequent conflict test. For these tests I disabled mDNS over IPv6 to cut down on the captured packet clutter. The packets were captured in the same PC running the BCT.
First the failing test with BCT output:
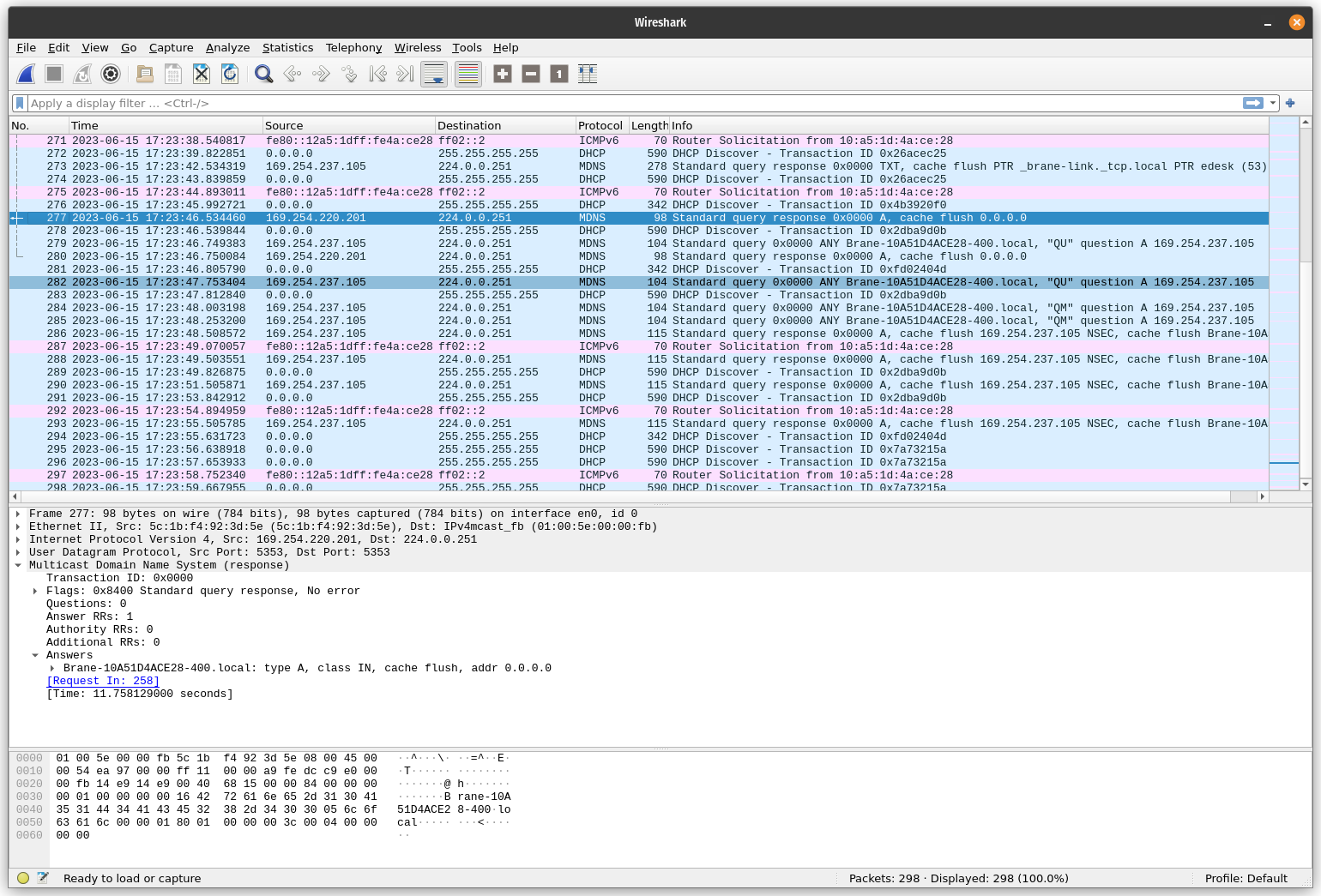
START (SUBSEQUENT CONFLICT)
NOTICE 2023-06-15 17:23:46.533867-0500 _sub_conflict 03498: Sending conflicting announcements for Brane-10A51D4ACE28-400.local.
ERROR 2023-06-15 17:23:47.753928-0500 _sub_conflict 03570: Device did not complete its probing sequence for a new name after a subsequent conflict arose for its previously acquired name.
FAILED (SUBSEQUENT CONFLICT)
Packet no. 277 is the conflict. Packet no. 279 and 282 are defensive probes. Note that the test fails when the second defensive probe is received.
Second the passing test with BCT output:
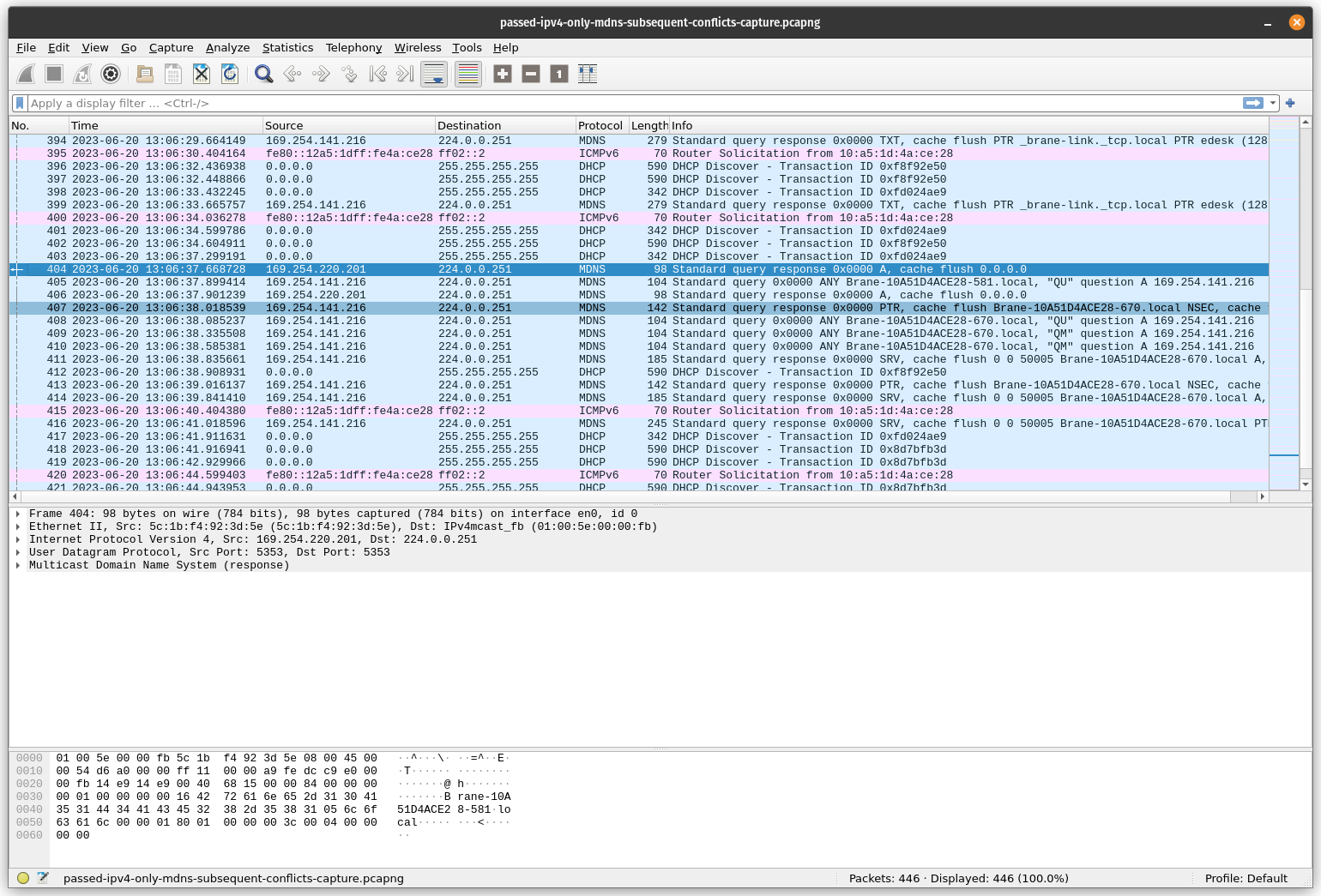
START (SUBSEQUENT CONFLICT)
NOTICE 2023-06-20 13:06:37.668160-0500 _sub_conflict 03498: Sending conflicting announcements for Brane-10A51D4ACE28-581.local.
NOTICE 2023-06-20 13:06:38.836215-0500 recv_announcement 03419: Received announcement for Brane-10A51D4ACE28-670.local.
NOTICE 2023-06-20 13:06:38.836316-0500 _sub_conflict 03598: Device acquired new name Brane-10A51D4ACE28-670.local.
NOTICE 2023-06-20 13:06:48.841450-0500 _sub_conflict 03498: Sending conflicting announcements for edesk (128)._brane-link._tcp.local.
NOTICE 2023-06-20 13:06:54.201280-0500 recv_announcement 03419: Received announcement for edesk (210)._brane-link._tcp.local.
NOTICE 2023-06-20 13:06:54.201382-0500 _sub_conflict 03598: Device acquired new name edesk (210)._brane-link._tcp.local.
PASSED (SUBSEQUENT CONFLICT)
Packet no. 404 is the conflict. Packet no. 405 is the defensive probe. Packet 407 is the DUT releasing the record. Note that the DUT running this modified mdnsd passes all the mDNS (ipv4 and ipv6) related tests.
I'm interested in collecting more data to better understand and fix this problem if you have any suggestions.
Regards,
Ethan